ScanEx Configuration
This configuration is used when calling the Metadefender Core APIs that do not use the Metadefender Core workflows, and only scan files. This includes files scanned through Metadefender Core's ICAP interface, files scanned with Metascan Client, files scanned through the Java API, and the sample code provided on the OPSWAT Portal.
Archive handling
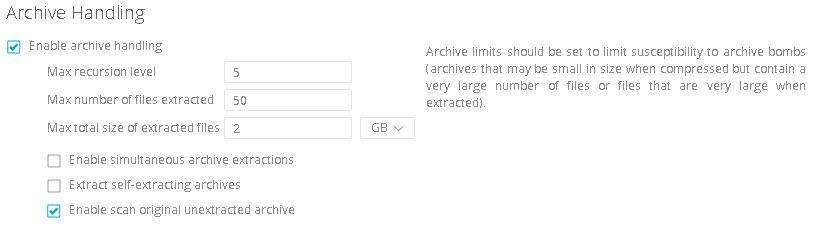
The archive handling configuration options determine how archives are handled.
If archive handling is enabled, Metadefender Core will extract archives and scan the individual files within the archive.
Most common archive formats are supported, including 7z, XZ, BZIP2, GZIP, TAR, ZIP, WIM, ARJ, CAB, CHM, CPIO, CramFS, DEB, DMG, FAT, HFS, ISO, LZH, LZMA, MBR, MSI, NSIS, NTFS, RAR, RPM, SquashFS, UDF, VHD, WIM, XAR and Z. Metadefender Core can also extract self-extracting archives created by both 7zip and WinRAR.
The following settings apply if archive handling is enabled:
|
Property |
Description |
Default Value |
CLI config |
Additional info |
|
Enable Archive |
This enables Metadefender Core's archive library handling. |
Enabled |
le=<0|1> |
|
|
Max Recursion Level |
The maximum depth that Metadefender Core will continue to extract archives for scanning. Once this depth is reached, Metadefender Core will not extract further archives but will scan those archives as entire files. If this is set to 0, archives will not be extracted. |
5 |
rl=<levels> |
Maximum value: 2147483646 |
|
Number of Files |
The maximum number of files that can be in an archive that Metadefender Core is extracting. If the number of files in an archive exceeds this value, Metadefender Core will return the result as a potential threat. |
50 |
an=<number> |
Maximum value: 2147483646 |
|
Total Size |
The maximum total size of files that can be in an archive that Metadefender Core is extracting. If the total size of files in an archive exceeds this value, Metadefender Core will return the result as a potential threat. |
2 GB |
as=<size in MB> |
Maximum value: Half the current available free space of the Metadefender Core temporary directory. If two temporary directories are set from different drives, the highest available space will be used. |
|
Simultaneous |
Specifies if multiple archive files undergo extraction concurrently. This may improve performance on a multi-core CPU, but means that the RAM-drive size should be increased (since more unpacked archives may reside on it at the same time). |
Disabled |
ec=<0|1> |
|
|
Self-Extracting |
Specifies if self-extracting archives should be extracted and treated as archives |
Disabled |
sx=<0|1> |
|
|
Scan Original Un-extracted File |
In addition to scanning files inside of an archive after extraction, un-extracted archives are sent directly to engines for scanning. Note: If “extract_archive” for an engine is enabled, this potentially exposes performance overhead since extraction happens twice, once by Metadefender Core and once by the engine.
|
Disabled |
soa=<0|1> |
|
Note: DOCX and DOCM files can be detected as archive files. OPSWAT recommends that the option to scan the original un-extracted archive is enabled so that these files are properly scanned.
Post processing configuration
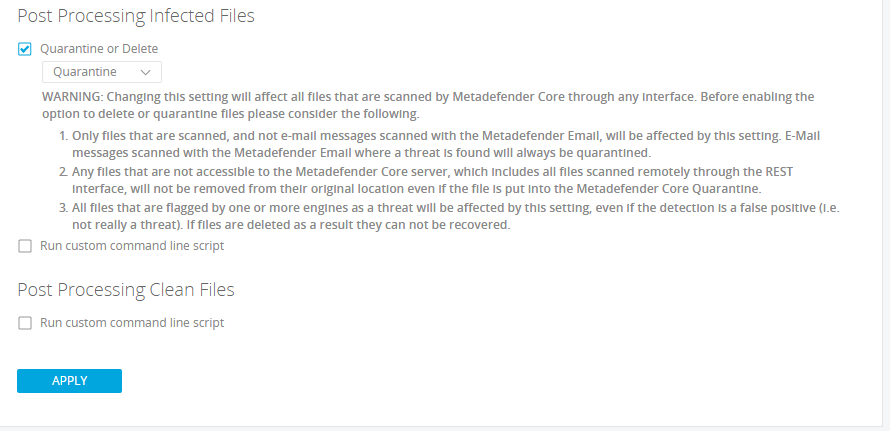
The Post Processing configuration allows an administrator to specify a script that should be executed for all allowed and/or blocked files. By clicking on ‘Run custom command line script’, a message can be put in place for both infected and clean files.
An administrator can also choose to delete or quarantine infected files.