WAN Interface - The Gateway to the World
When it comes to networking, the WAN interface is a crucial component that acts as the gateway to the world. It provides the connection to the outside world and allows devices to communicate with the internet and other networks.
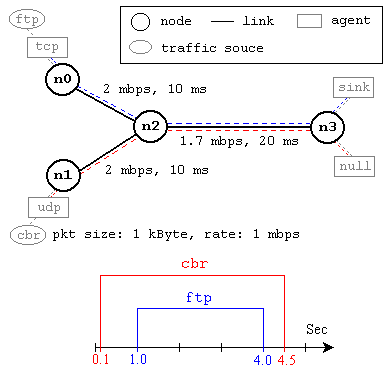
In simple terms, the WAN interface is the port on a router or gateway device that connects to the Wide Area Network (WAN). This interface can be physical or virtual and is designed to handle data traffic from the local network to the internet.
The WAN interface enables communication between devices in different locations, making it essential for remote work and collaborations. It comes with various protocols and technologies such as Ethernet, DSL, Fiber, and Cable modems, offering different levels of speed and reliability.
Moreover, WAN interfaces can be configured for security purposes, allowing administrators to set up firewalls, VPNs, and other security measures to protect the local network from threats.
In today's digital age, where organizations operate globally, having a reliable WAN interface is critical for business operations. From sending emails and conducting online transactions to video conferencing and cloud computing, WAN interfaces form the very foundation of online communications.
In conclusion, a WAN interface is the backbone of online connectivity, opening up a world of possibilities for communication and collaboration. With its speed, security, and reliability, it has become an indispensable tool for businesses, enterprises, and individuals alike.