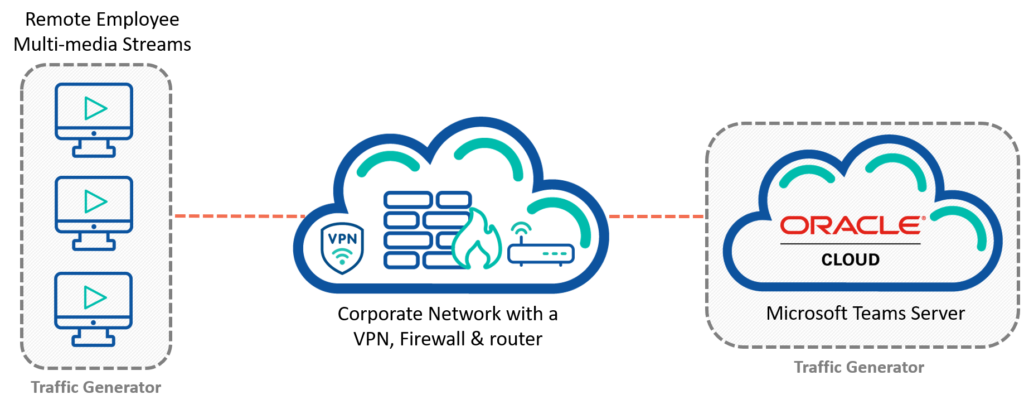
As our world becomes increasingly connected, the need for secure wireless transmission is paramount. The wireless transmission security scanner is a vital tool in meeting this need. It offers a proactive approach to identify potential security risks, and offers solutions for mitigating them.
The scanner offers a range of benefits for individuals and organizations alike. It helps to detect unauthorized access to networks, as well as rogue wireless devices that may pose a threat. The tool can identify vulnerabilities in wireless networks, such as weak passwords or outdated software, and provide recommendations for improving security.
By utilizing a wireless transmission security scanner, organizations can limit the risk of their sensitive information being intercepted or compromised. It can help to prevent data breaches, which can cause significant financial and reputational damage to any company. Furthermore, the scanner can also aid in compliance with regulatory requirements, such as HIPAA or PCI DSS.
In conclusion, the wireless transmission security scanner is a valuable tool for any individual or organization that prioritizes security. By scanning and identifying potential threats, it empowers users to implement appropriate security measures before any damage can occur. It is a logical investment in the protection of sensitive data, and against the ever-present threat of cyber-attacks.