Network Security Vulnerability Scanner
With the rapid advancement of technology, it has become increasingly essential for organizations to secure their computer networks effectively. Information systems must be protected against unauthorized access, hacking, and malicious software attacks. A network security vulnerability scanner is an essential tool in identifying potential vulnerabilities in a network.
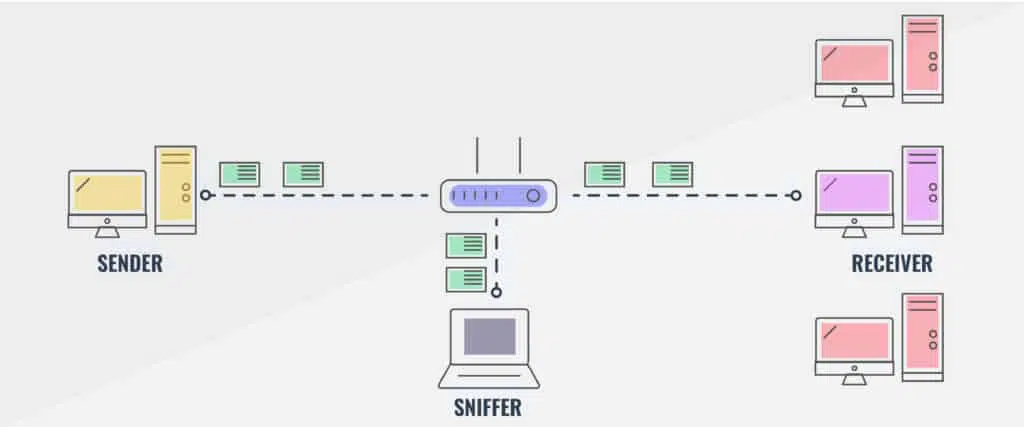
A vulnerability scanner is a software program that assesses the security of a network by scanning its various components. It examines servers, network devices, applications, and communication protocols for potential vulnerabilities. Once vulnerabilities are detected, they are graded according to their severity and reported to the administrator. Security experts use this information to prioritize the overall security posture of the network.
This tool is significant because it saves time and effort by automating the process of identifying vulnerabilities. Instead of relying on time-consuming manual checks, the scanner can provide a comprehensive view of the network's security posture. It can also perform daily scans to identify any new vulnerabilities that may have occurred.
Additionally, the vulnerability scanner is easy to use and does not require any specialized skills or knowledge. The administrator can quickly interpret and act on the reported vulnerabilities. The scanner can also provide recommendations on how to mitigate the vulnerabilities, such as applying security patches, upgrading software, or reconfiguring network devices.
In conclusion, a network security vulnerability scanner is an essential tool for any organization that wants to secure its computer network. It provides an automated solution to identify potential vulnerabilities and recommend solutions. By incorporating this tool into a proactive security approach, organizations can significantly reduce the risks from cyber threats.