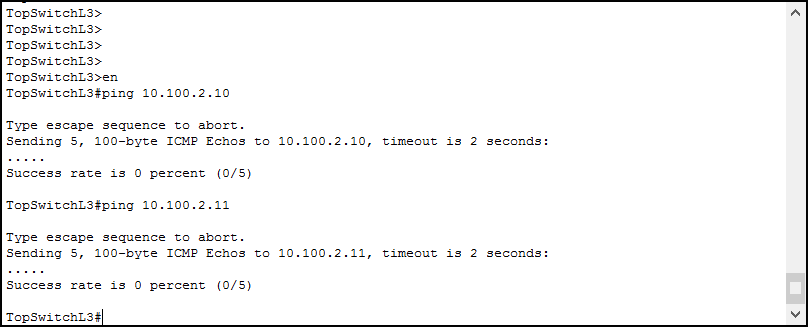
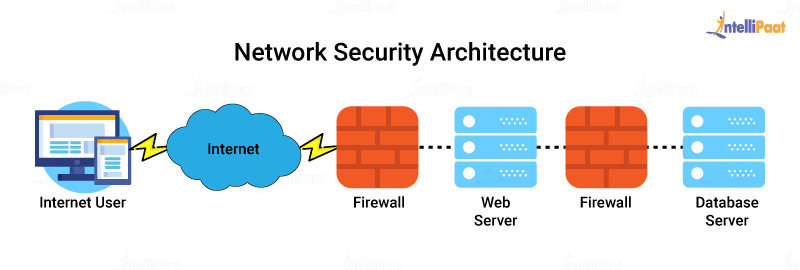
When it comes to managing a network, issues may arise at any time, and it's crucial to have the right tools to troubleshoot the problem. An IT team that can rapidly identify and fix network issues is key to maintaining productivity and ensuring company profitability.
The following are some network troubleshooting tools to help IT teams diagnose issues:
- Network Protocol Analyzers: These tools examine network traffic and data packets to detect issues such as errors, network congestion, and security breaches.
- Network Monitoring Software: These tools enable IT teams to keep a constant eye on the network's performance, helping to identify issues before they become significant problems.
- Remote Access Tools: A team that can access a remote system is equipped to troubleshoot a problem, can investigate the issue without having to be physically present.
- Configuration Management Tools: These tools enable IT teams to track and manage changes in the network, ensuring that issues resulting from configuration errors are avoided.
- Bandwidth Monitoring Tools: These tools track network bandwidth usage, which helps to detect and resolve problems faster while optimizing available bandwidth.
These tools help IT teams to identify and quickly solve network problems before they cause bottlenecks and significant downtime. In addition to these technical tools, collaboration combined with a sound methodology decreases the time taken to identify, diagnose, and fix problems. It is evident that networking remains the backbone of businesses, and a well-run IT department should be equipped with these and other network troubleshooting tools to provide quality services and fast solutions.