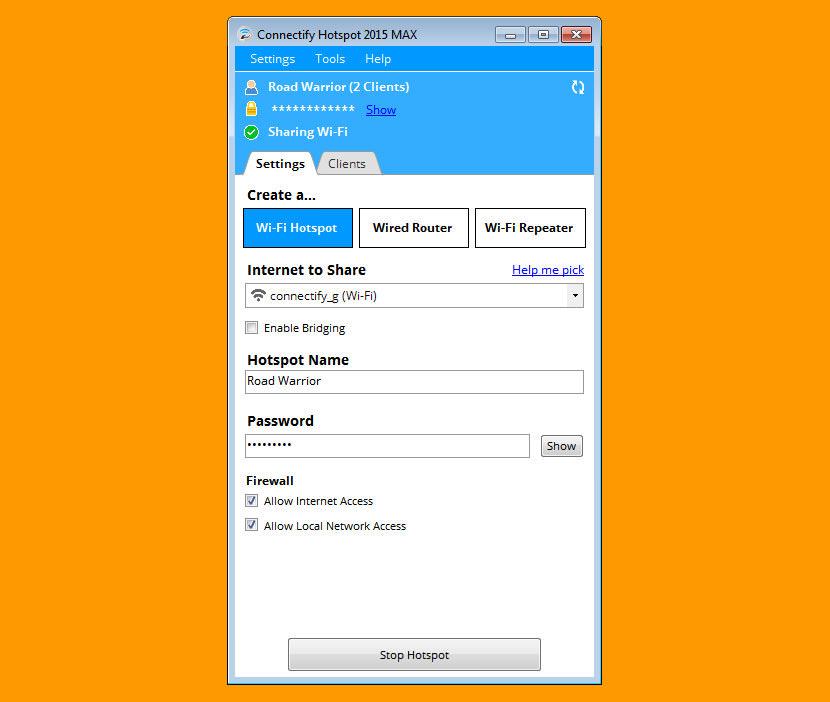
Router Management Interface
Managing a router is an important aspect of maintaining a network. The router management interface is a web-based tool used to configure, monitor and troubleshoot a router. It is a gateway to the router's configurations and settings and allows you to access these settings and change them as needed. The purpose of this article is to provide insight into what the router management interface is and the benefits of using it.
One of the key benefits of the router management interface is its user-friendliness. It provides users with a graphical representation of the router's settings and configurations, making it easy to navigate and understand. This makes it easy for both novice and advanced users to configure and manage a router.
The router management interface also enables you to troubleshoot issues and monitor the performance of your router. It provides real-time data on traffic, bandwidth usage, and connected devices. This data can be used to identify devices or applications that are consuming too much bandwidth and causing network congestion.
Another important benefit of the router management interface is the ability to secure your network. It provides settings for enabling encryption, setting up access control, and configuring firewalls to protect your network from unauthorized access.
In conclusion, the router management interface is an essential tool for managing and maintaining a router. Its user-friendly interface, real-time monitoring, troubleshooting tools, and security features make it an indispensable tool for both novice and experienced network administrators. By using the router management interface, you can efficiently manage your network and ensure that it is secure and running smoothly.