Router Ports Open: Can You Hear the Hackers Knocking?
Choosing the right router is not enough to secure your network. One of the most neglected security aspects is the router ports open. Open ports are like an unlocked door that could welcome any trespassers. Few people know how to configure router ports, and let’s face it, the idea of opening or closing some ports sound like gibberish to most. That’s why we need to stress the importance of protecting our router and network by securing our router ports.
Let’s take a quick look at what ports are. A port is a communication gateway on your network. Like a phone line in a switchboard, ports allow communication between devices within your network, and with the outside world. Each port is identified by a unique number, and each number has a predefined purpose. Think of it like a secret knock that only some people may use to get in.
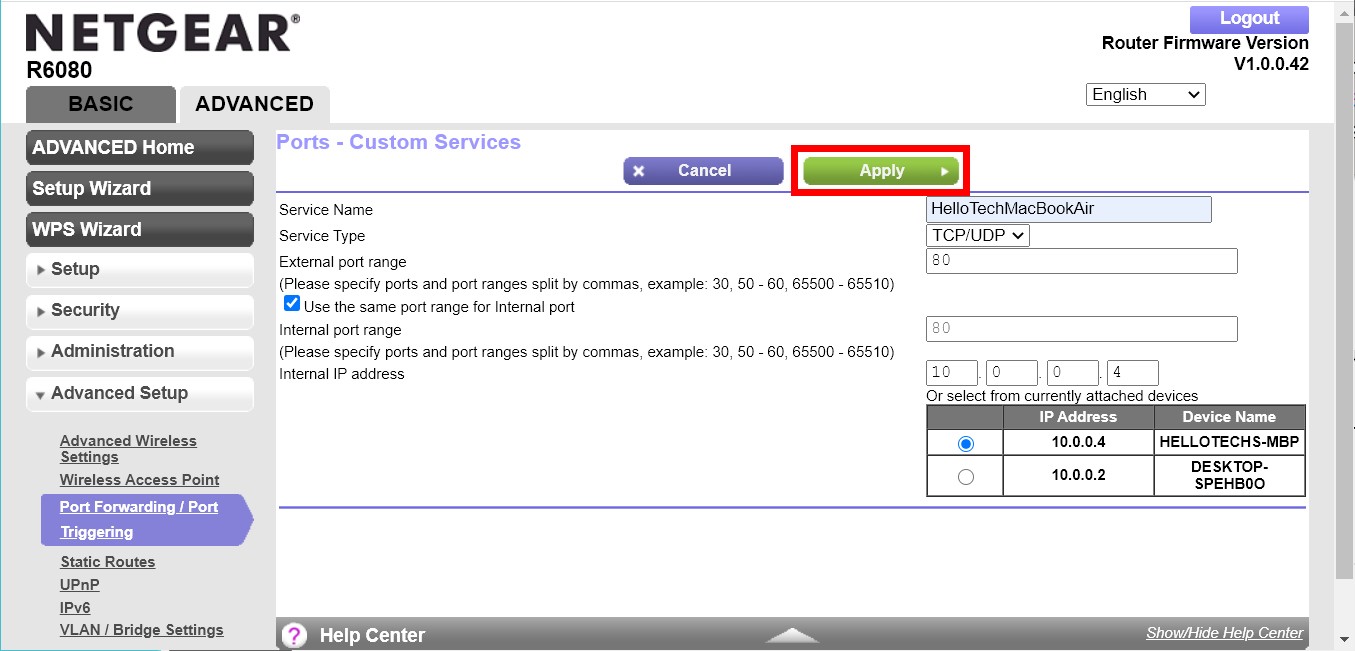
The problem starts when too many ports are open, or the wrong ones. For example, if a port that is usually reserved for internal communication is open, it could be exploited by an outsider to infiltrate your entire network. This is why shutting down unnecessary ports enhances your network security.
But what if you need to open a port for an incoming connection? The best practice is to add a firewall rule to only allow the necessary data to get through, instead of leaving a port permanently open. Also, remember to close the port once it’s no longer needed.
So, let’s wrap this up. Protect your network as you would your castle. Don’t let the bad guys in, and prevent the open ports from becoming an open invitation to hackers. And if you don’t know how to do it, learn or hire an expert. It’s worth it.