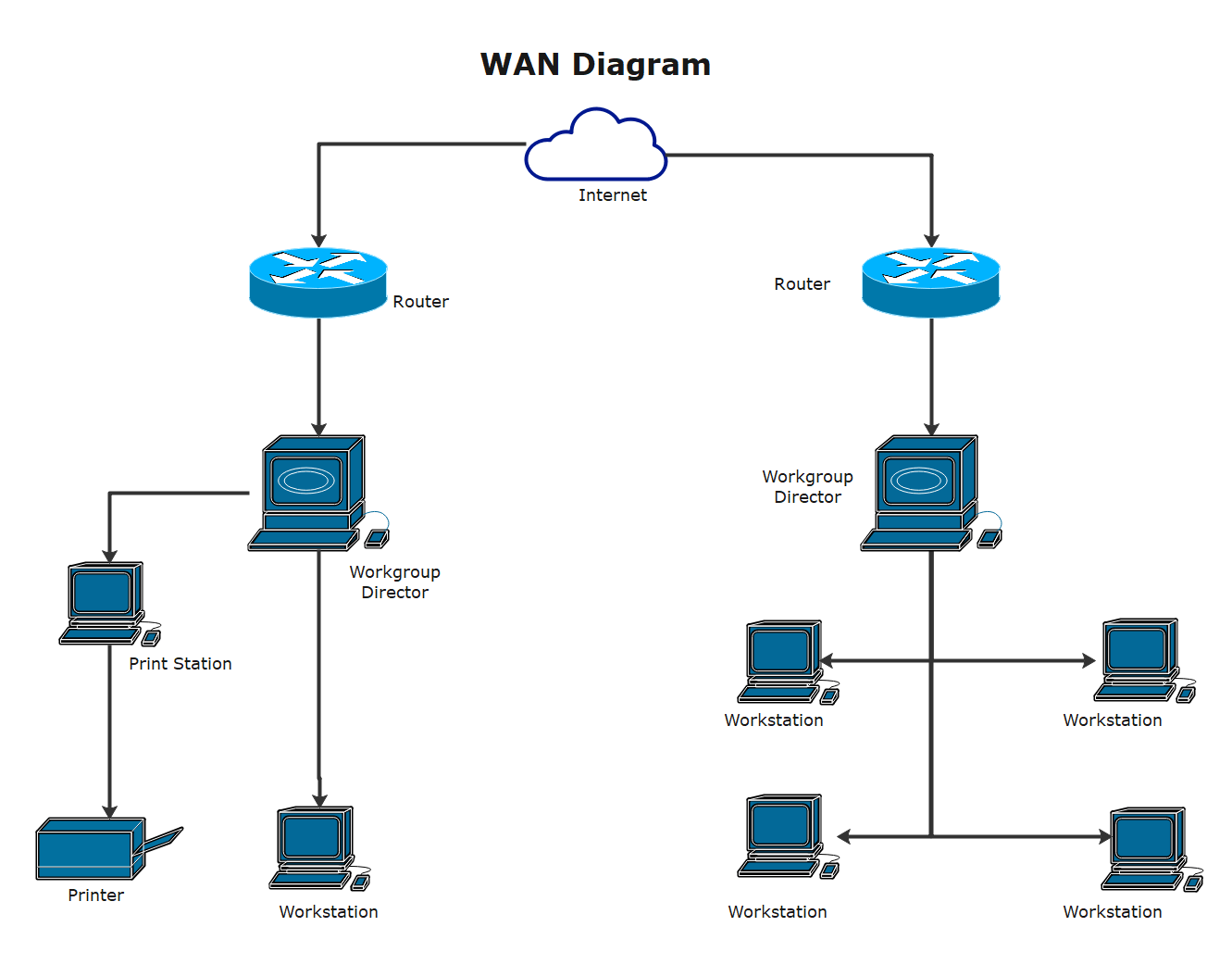
Are you looking for a way to enhance your understanding of network virtualization? If yes, then a network virtualization lab is the perfect solution you need.
A network virtualization lab is an innovative tool that enables you to create and deploy various kinds of virtual network scenarios, which can help to deepen your knowledge about network virtualization. Essentially, this lab replicates the experience of working with a virtual network in a real-world setting.
The lab has a self-contained environment where you can experiment with network virtualization configurations without the risk of impacting your production network. And, because it's virtual, you can easily create different network topologies to see how different configurations impact network performance.
The beauty of this lab is that it allows you to learn in a safe, controlled environment before you implement new changes on your production network. In addition, it provides practical experience, which reinforces your understanding of network virtualization concepts, making it easier to apply your knowledge in the real world.
Moreover, it is easy to set up a network virtualization lab as it is typically a software-based solution that can run on most common hardware or cloud-based infrastructure. With minimal costs, you can acquire the necessary infrastructure to run a virtualized network in-house or off-premises.
In conclusion, a network virtualization lab is an excellent tool for anyone looking to gain practical and theoretical knowledge about virtual networking. By providing a safe and reliable testing environment, a network virtualization lab can help you to expedite the deployment of virtual networks and ensure you can make changes to your network with confidence.