Wireless Speed Testing
Wireless speed testing is a crucial aspect of modern-day internet usage. With the increased dependency on the internet, both in personal and professional life, internet speed becomes significant. Inadequate internet speed can cause frustration in the users and also bring business operations to a halt. Therefore, it's essential to measure the wireless speed regularly to ensure smooth and efficient operations.
Speed testing your Wi-Fi is easy and can be done in minutes. There are several speed testing websites and applications that you can use to measure your internet connection speed. Online speed tests measure the download and upload speeds of your connection, along with the latency.
Latency is the time it takes for data to travel between you and the testing server, and it's crucial for tasks that require rapid communication with a remote server, such as gaming or video conferencing. So, you must choose a speed testing service that takes latency into account.
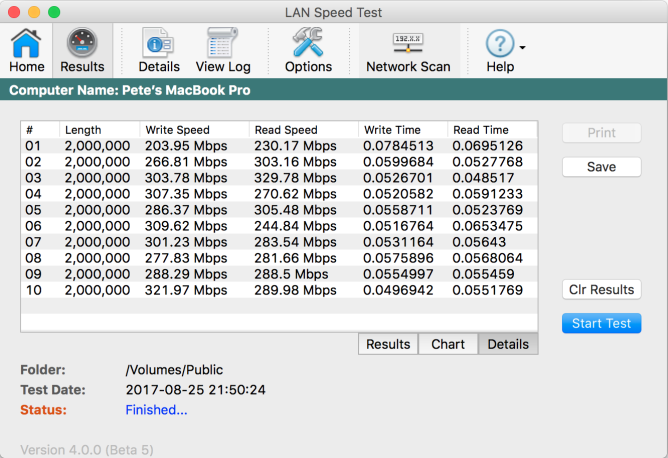
Advanced users can also run a more comprehensive wireless speed test by using specialized tools that provide more detailed analysis of connection issues. Such tests help identify signal strength issues, channel interference, and discover areas of your home or office with suboptimal connectivity.
In conclusion, regular wireless speed testing helps you monitor your internet connection speed, guaranteeing seamless internet access both at home or at work. Internet technology constantly evolves, so it's imperative to test your speed regularly and make the necessary adjustments to ensure you're getting the best possible wireless connectivity.