 |
WE310F5
39.00.000
|
 |
WE310F5
39.00.000
|
This section describes the M2MB APIs for Transport Layer Security (TLS) and the Secure Socket Layer (SSL). More...
This section describes the M2MB APIs for Transport Layer Security (TLS) and the Secure Socket Layer (SSL).
SSL/TLS module provides secure connection at L4 layer. To establish a secure connection the following steps are to be followed.
To establish a secure connection the following steps are followed.
As client: ----------
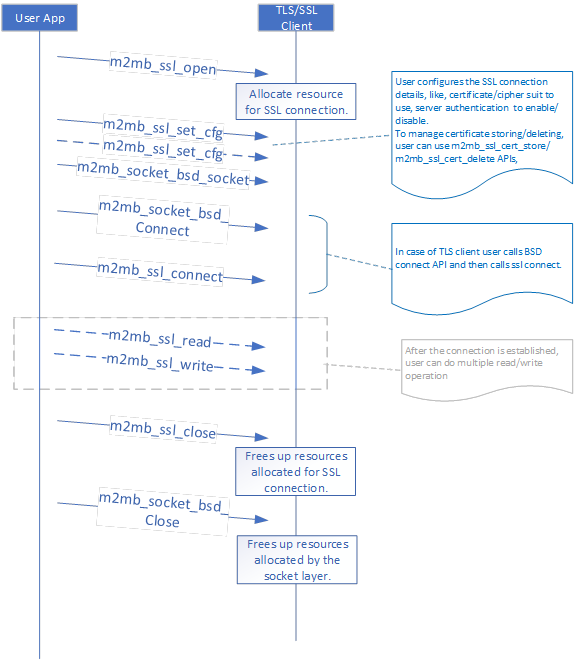
To connect to a server, use the following API sequence:
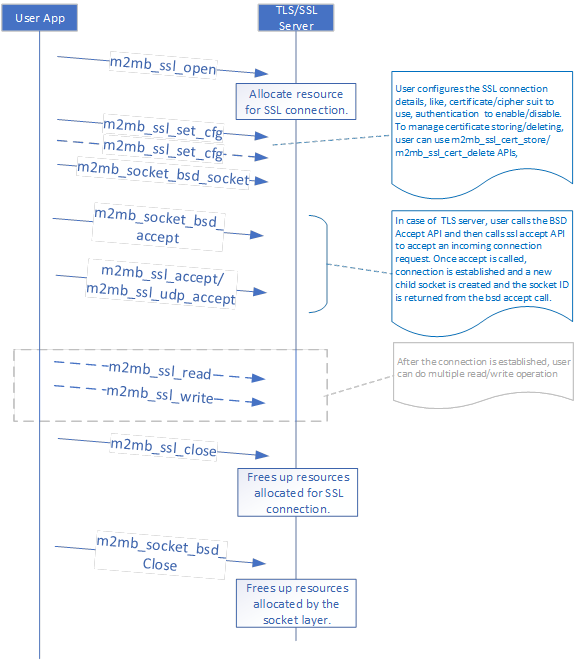
To start a server, use the following API sequence:
- First to allocate resources for SSL connection, m2mb_ssl_open should get
called with M2MB_SSL_SSL_ROLE_SERVER_E flag in M2MB_SSL_OPEN_PARAMS_T.
- To configure SSL parameter user must use m2mb_ssl_set_cfg.
- User needs to create the socket either UDP/TCP by calling socket API i.e. m2mb_socket_bsd_socket
- Next user needs to bind should be performed on specified local port and IP
address by using m2mb_socket_bsd_bind. This might be optional.
- Next user needs to listen for connections on that socket by calling socket API i.e m2mb_socket_bsd_listen.
- when client connectes to the ssl server, The ssl server must do m2mb_bsd_socket_accept,
to accept the TCP connection.
- Server will use the newly accepted client socket id for doing ssl handshake
by calling the m2mb_ssl_accepts API.
- For information of the ssl connection information m2mb_ssl_get_cfg can be used.| #define M2MB_MAX_CERTS 10 |
Definition at line 106 of file m2mb_ssl.h.
| #define M2MB_SSL_CIPHER_MAX 0x003FFFFFFFFFFFFF |
Definition at line 105 of file m2mb_ssl.h.
| #define M2MB_SSL_INVALID_HANDLE (0) |
Macro for invalid SSL handle
Definition at line 101 of file m2mb_ssl.h.
| #define M2MB_SSL_MAX_CA_LIST 10 |
Macro for mavimum number of CA certs
Definition at line 107 of file m2mb_ssl.h.
| #define M2MB_SSL_MAX_CERT_NAME_LEN 64 |
Macro for Maximum length of name of a certificate
Definition at line 103 of file m2mb_ssl.h.
| #define M2MB_SSL_MAX_CIPHER_COUNT 54 |
Macro for Maximum ciphers
Definition at line 102 of file m2mb_ssl.h.
| #define M2MB_SSL_MAX_SNI_NAME_LEN (64) |
Macro for Maximum length of SNI name
Definition at line 104 of file m2mb_ssl.h.
| typedef enum M2MB_SSL_AUTH_TYPE_E M2MB_SSL_AUTH_TYPE_E |
SSL authentication types enum.
| typedef enum M2MB_SSL_CIPHER_SUITE_E M2MB_SSL_CIPHER_SUITE_E |
TLS ciphersuites enum.
| typedef enum M2MB_SSL_CONF_ID M2MB_SSL_CONF_ID_E |
| typedef union M2MB_SSL_CONF_PARAMS M2MB_SSL_CONF_PARAMS_T |
| typedef struct M2MB_SSL_CONFIG M2MB_SSL_CONFIG_T |
Structure to configure an SSL connection.
| typedef struct M2MB_SSL_CONFIG_VERIFY_POLICY M2MB_SSL_CONFIG_VERIFY_POLICY_T |
Structure to specify the certificate verification policy.
| typedef HANDLE M2MB_SSL_CTXT_HANDLE |
SSL context handle.
This is obtained from m2mb_ssl_open API and then used in subsequent SSL APIs.
Definition at line 165 of file m2mb_ssl.h.
| typedef struct M2MB_SSL_OPEN_PARAMS M2MB_SSL_OPEN_PARAMS_T |
| typedef enum M2MB_SSL_PROTOCOL_VERSION_E M2MB_SSL_PROTOCOL_VERSION_E |
SSL protocol SET Configuration enumeration.
This enum defines macros for various SET Configuration for MDNS module.
| typedef enum M2MB_SSL_SSL_ROLE_E M2MB_SSL_SSL_ROLE_E |
SSL object role.
| enum M2MB_SSL_AUTH_TYPE_E |
SSL authentication types enum.
| Enumerator | |
|---|---|
| M2MB_SSL_AUTH_NONE | |
| M2MB_SSL_AUTH_REQUIRED | |
| M2MB_SSL_AUTH_OPTIONAL | |
Definition at line 230 of file m2mb_ssl.h.
TLS ciphersuites enum.
Definition at line 169 of file m2mb_ssl.h.
| enum M2MB_SSL_CONF_ID |
Definition at line 126 of file m2mb_ssl.h.
SSL protocol SET Configuration enumeration.
This enum defines macros for various SET Configuration for MDNS module.
Definition at line 116 of file m2mb_ssl.h.
| enum M2MB_SSL_SSL_ROLE_E |
SSL object role.
| Enumerator | |
|---|---|
| M2MB_SSL_SSL_ROLE_SERVER_E | Server role. |
| M2MB_SSL_SSL_ROLE_CLIENT_E | Client role. |
Definition at line 238 of file m2mb_ssl.h.
| M2MB_STATUS_T m2mb_ssl_accept | ( | M2MB_SSL_CTXT_HANDLE | sslSvrContextHndl, |
| M2MB_SOCKET_BSD_SOCKET | socket_fd, | ||
| M2MB_SSL_CTXT_HANDLE * | sslClientCtxHndl | ||
| ) |
Accepts an incoming SSL connection from the client.
It creates a client context, sets configuration passed to the incoming client context, links a secure socket connection id to socket fd and accepts the incoming client connection. This should be called only by a server SSL object. This will respond to the incoming client hello message and complete the SSL handshake.
| [in] | sslSvrContextHndl | specifies the SSL context of the server previously created through m2mb_ssl_open |
| [in] | socket_fd | specifies the socket fd for the incoming client |
| [out] | sslClientCtxHndl | client context handle |
Example
| M2MB_STATUS_T m2mb_ssl_close | ( | HANDLE | handle | ) |
deletes an m2mb SSL context created during m2mb_ssl_open()
| [in] | handle |
Example
| M2MB_STATUS_T m2mb_ssl_connect | ( | HANDLE | handle, |
| M2MB_SOCKET_BSD_SOCKET | socket_fd | ||
| ) |
Performs SSL Client connection.
Performs SSL client connection
| [in] | handle | Specifies the sslContextHndl previously returned by m2mb_ssl_open |
| [in] | socket_fd | Specifies the socket ID to make the connection. |
Example
| M2MB_STATUS_T m2mb_ssl_get_cfg | ( | HANDLE | handle, |
| M2MB_SSL_CONF_ID_E | conf_id, | ||
| M2MB_SSL_CONF_PARAMS_T * | conf_params | ||
| ) |
Get SSL configuration on the previously created SSL context.
Get the SSL/TLS configuration given the specified configuration id.
| [in] | handle | Specify the SSL context pointer created previously during m2mb_ssl_open(); |
| [in] | conf_id | Specify the confd id as defined in M2MB_SSL_CONF_ID_E. |
| [out] | conf_params | pointer to structure of type M2MB_SSL_CONF_PARAMS_T |
Example
| M2MB_STATUS_T m2mb_ssl_open | ( | HANDLE * | handle, |
| M2MB_SSL_OPEN_PARAMS_T * | openParams | ||
| ) |
Initialize SSL TLS context.
Creates SSL TLS context that which will be used in all the future calls to m2mb SSL module
| [out] | handle | hndl will be filled on successful completion |
| [in] | openParams | pointer to openParams structure |
Example
Read len bytes from SSL connection into buf.
| [in] | handle | Specifies the sslContextHndl previously created during m2mb_ssl_open |
| [out] | buf | Specifies the read buffer |
| [in] | len | Specifies the input len |
Example
| M2MB_STATUS_T m2mb_ssl_set_cfg | ( | HANDLE | handle, |
| M2MB_SSL_CONF_ID_E | conf_id, | ||
| M2MB_SSL_CONF_PARAMS_T * | conf_params | ||
| ) |
Set SSL configuration on the previously created SSL context.
Set an SSL TLS configuration with specified configuration parameters and sets the config on the provided SSL context handle.
| [in] | handle | Specify the SSL context pointer created previously during m2mb_ssl_open(); |
| [in] | conf_id | Specify the confd id as defined below: |
0 : Invalid config param 1 : To Set SSL Protocol Vertion 2 : To Set SSL CA Certificate 3 : To Set SSL Certificate 4 : To Set Cipher Information 5 : To set tx max fragment length
6 : To Set the SNI 7 : To set the Domain 8 : To set max fragment length 9.: To Enable/Disable server Authentication 10 : To Enable/Disable Time Validation ( not supported )
| [in] | conf_params | pointer to structure of type M2MB_SSL_CONF_PARAMS_T The values in the structure must be set as per the conf_id |
Example
Writes data to the SSL connection.
| [in] | handle | Specifies the sslContextHndl |
| [in] | buf | Specifies the input buffer |
| [in] | len | Specifies the input len |
Example