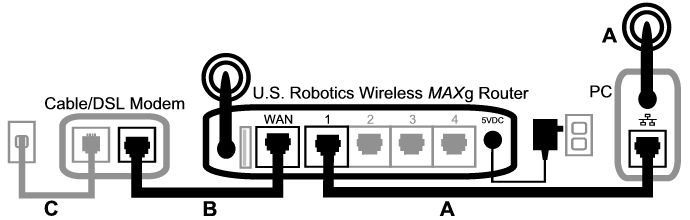
Router Ports Used
When it comes to networking, routers are one of the most important devices. They allow multiple devices to connect to the internet, and they are often used in homes, offices, and other locations. Router ports are essentially the channels used by routers to allow data to travel between two devices.
Routers come with different types of ports, each serving a different purpose. These ports include WAN ports, LAN ports, USB ports, and more. WAN ports are used to connect your router to the internet, while LAN ports are used to connect devices within your home or office network. USB ports are used for attaching external devices such as printers, hard drives, or modems.
Most consumer-grade routers tend to come with a standard set of four LAN ports and one WAN port. However, some routers come with up to eight LAN ports, and others may have multiple WAN ports. The type and number of ports that a router has can have an impact on its speed and functionality.
Understanding the different router ports can help you configure your network more effectively. For instance, if you have a large number of devices that you need to connect to your network, it may be best to get a router with multiple LAN ports. If you need to connect to different types of networks, such as 3G and 4G networks, a router with multiple WAN ports may be the best choice.
In conclusion, knowing the types and functions of router ports can help you set up and manage your network more easily. Be sure to check the specifications before buying a router to make sure it has the ports that you need.