SOURCE
FBI IC3 2014 INTERNET CRIME REPORT
saysBruceSchneier,
best-sellingauthorof
DataandGoliath:The
HiddenBattles toCollect
YourDataandControl
YourWorld
. “Weneed
regulationsmandating
betterInternetsecurity
in thedeviceswebuy
and thenetworkedser-
vicesweuse.”
Cyber-security
expertsarea lot less
alarmist thanI thought
they’dbe.Manyof them
sawsilver liningsamong
thedarkestofclouds,
saying thathigh-profile
incidentsactually
change thesecurity
landscape for thebetter.
“Thegoodnews is
thatarecentstringof
attackshasgalvanized
security-standards
organizations, theWhite
Houseandcorporate
leadership,”saysEric
Friedberg, executive
chairmanof thedigital
forensicsfirmStroz
Friedberg. “Asaresult,
there ismorepublic-privatecollaboration.”
It’snot justdispassionateexpertswho
areshowingsomeresilience in the faceof
hackers.Thepublic isstillbuyingstuffon
theInternetevenas theyreadaboutstolen
identitiesandcompromisedaccounts. “So
far, surprisingly, these incidentshavenot
hadamaterialeffectonoverallconsumer
confidence,”Friedbergpointsout. “This is
probablybecause theactual fraud losses
forcustomersarenotsignificantcompared
to theoverallvolumeofe-commerce.”
Thecat-and-mousegamebetweencyber
attackersandprotectors is justbeginning,
andovertimethedefensewillcatchup.The
samethinghappenedwithbankrobbers;
assecuritytech improved, thenumberof
robberiesdroppedandtheheistsbecame
moreprofessionallycomplex.
“Security,even ifwedonotrealize it,
slowly improves.Attacksbecomingmore
andmoresophisticatedareasignof the
‘low-hanging fruit’beingtakenaway,”
Zanerosays. “This isanever-endingbattle.”
and lead tomore fatal trafficaccidents.
Facing thedarkeraspectsof thehuman
condition ispartofadopting technology.
“As timewenton, systemsweredesigned to
make traveling thehighwaysystemsafer,”
saysTimothyRyan,managingdirector
ofcybersecurityatKroll,wherehe leads
Kroll’scyber investiga-
tions. “Thesame thing is
happeningwith informa-
tionnetworks.”
Rightnow,human-
ity isstill early in the
information-techgame,
andwheresecurity is
concerned,we’restarting
fromalmostscratch.
Theentirepurposeof
networkingeverything
was forpeople toshare
information (email,
smartphones), tocon-
ductcommerce (eBay,
Amazon)and torun
thingsbyremotecontrol
(industrial control
systems,home thermo-
stats). Itwascreated to
beopen toeveryone,with few limitsor
obstacles.
Butsecurity isasnecessaryanobsta-
cleasa lanemarkingorared light is toa
roadway.Andasdigitallynetworked things
becomemore ingrained intoour lives—
enmeshed inclothes, embedded invehicles,
maybe implanted insidehu-
manbodies—securitywon’t
beanafterthought. “Thefirst
waveof thingsconnected
to theInternetwasnot
developedwithsecurity in
mind,”Zanerosays. “Butwe
knowhow tomanagemany
of therisksconnected to this
trend, andIexpectsecurity
of theInternetofThings to
rampup.”
There’snothing
inherentlyflawedwith the
hardwareof theInformation
Revolution thatrequireswe
beprey fordigitalcrooksand
madmen. “Thereare techni-
calproblems in information
security,butrightnow the
realproblemsarepolitical,”
JOEPAPPALARDO
isacontributingeditor
for
PopularMechanics
and theauthorof the
nonfictionbook
Sunflowers:TheSecretHistory
andanupcomingbookaboutspaceports.
90
SEPTEMBER2015
AMERICANWAY
TECHNOLOGY
Asweallenjoy the fruithanging from this
technology tree, it’s impossible to ignore theworms.
Hackers, thieves, crooksandspiesare lurking.
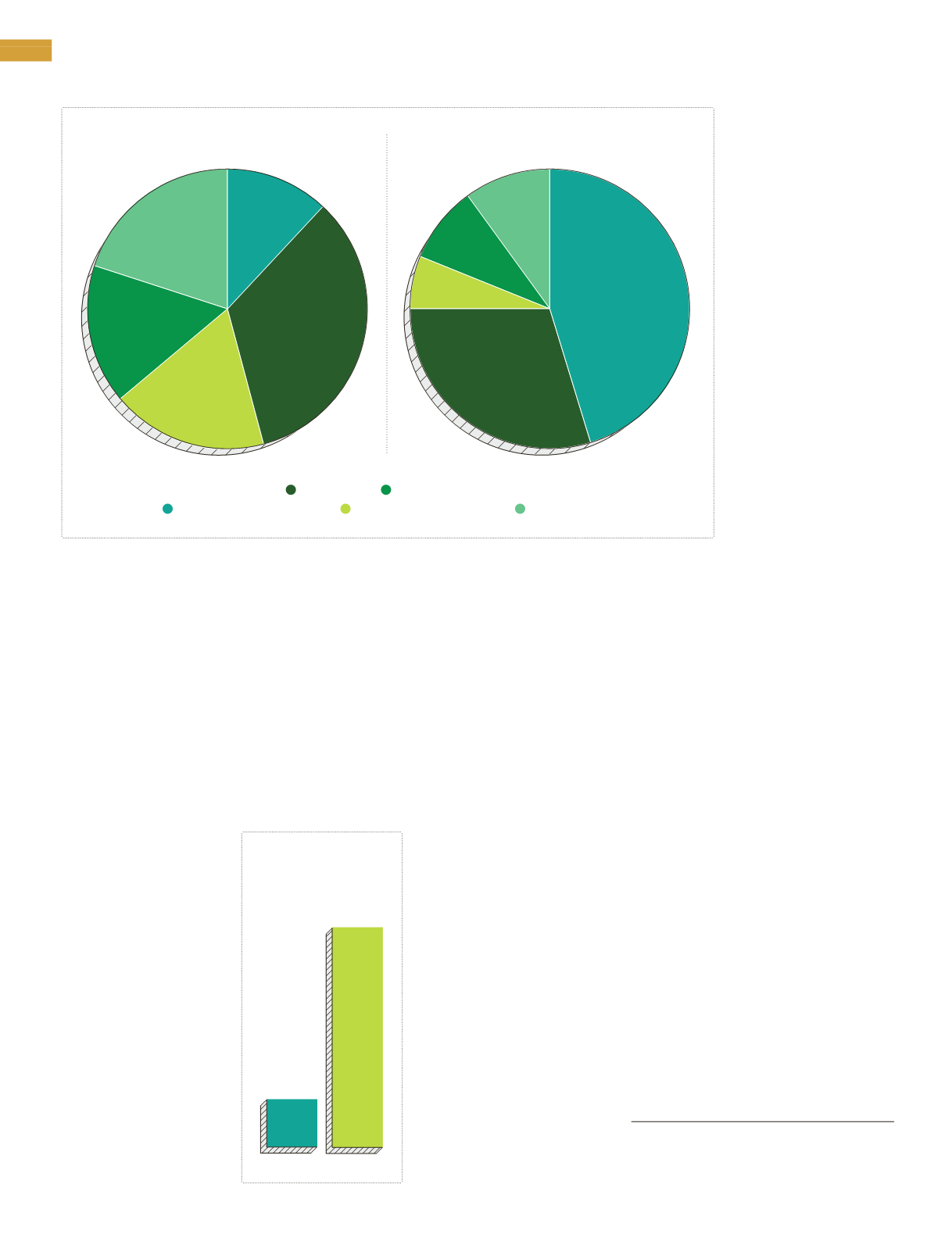
AutoFraud
Confidence/RomanceFraud
Intimidation/Extortion
Government Impersonation
Real EstateFraud
TOTALREPORTEDCOMPLAINTS IN2014
12%
10%
34%
45%
18%
30%
16%
6%
20%
9%
TOTALREPORTEDFINANCIALLOSS IN2014
MALE
VS.
FEMALE
TotalReported2014
Financial Loss in
Confidence/RomanceFraud
MALE FEMALE


