VIPRE Engine - Protection Policies
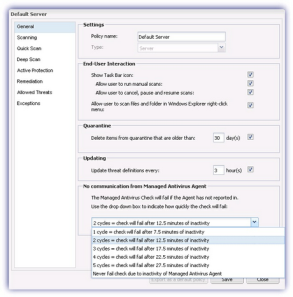
General
The General tab specifies the type of device the policy applies to and includes:
End-User Interaction
- Show Task Bar icon
- Allow user to run manual scans
- Allow user to cancel, pause and resume scans
- Allow user to scan files and folders in Windows Explorer right-click menu
Quarantine
Determines the way in which quarantined items are handled: Delete items from quarantine that are older than X days, along with the ability to disable this option.
Updating
How often to check for definition updates, Update threat definitions every X hours, along with the ability to disable this option.
The General section is also used to configured the suppression threshold for the No communication from Managed Antivirus Agent failures.
By default the Managed Antivirus Check will fail where we have not received any communication from the Managed Antivirus Agent after 2 cycles (12.5 minutes of inactivity) with the option to increase or decrease this threshold via the drop-down, including Never fail check due to inactivity of Managed Antivirus Agent.
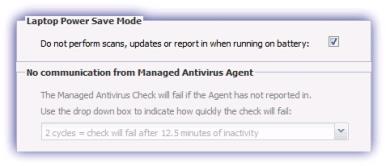
Laptop Power Save Mode
When the policy Type is set to Laptop the additional Laptop Power Save Mode option becomes available. This is designed to conserve power, where enabled the Managed Antivirus Agent does not perform scans, updates or report in to the Dashboard where the laptop is running on battery.
As the Managed Antivirus Agent does not communicate back to the Dashboard where Laptop Power Save Mode is selected, to prevent the generation of spurious notifications the No communication from Managed Antivirus Agent Alert is disabled where this option is enabled.
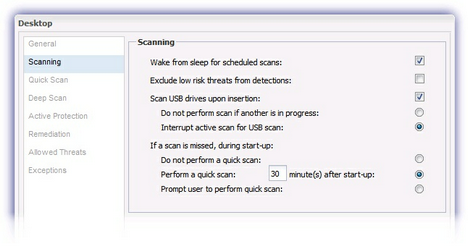
Scanning
The Scanning tab specifies options common to both quick and deep scan such as whether to scan USB drives upon insertion, whether to exclude low risk threats from detection and what to do if a scheduled scan is missed.
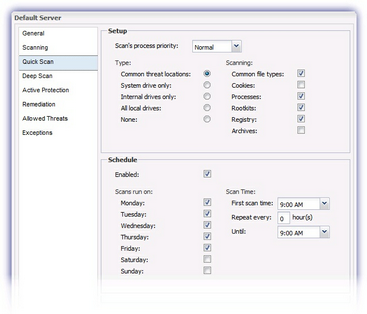
Quick Scan and Deep Scan
The Quick Scan tab and Deep Scan tab specify where to scan (drives and common threat locations etc), what to scan (common file types) and when to run quick scan and deep scan respectively.
Note: Managed Antivirus Scans run based on the local time of the computer the Agent is installed on.
Active Protection
The Active Protection tab specifies the behavior of the resident in-memory scanner, whether it is enabled*, if the end user is alerted when a threat is blocked and when to scan (on execution or when some or all files are touched).
There are three On access type options available for Active Protection
|
Execution Only |
Active Protection scans any file - not just executables - on execution i.e. where the file is accessed (opened, read, copied, moved or executed etc). This setting is optimal during normal conditions |
|
High Risk Extensions Only |
Active Protection will only scan those files with the specified extension (that are considered high risk) when they are executed or touched (e.g. directory listing) |
|
All Touched Files |
Active Protection scans all files when they are executed, copied onto the computer or touched. Use of this setting can result in slower system performance, depending on machine specifications, as well as the number and type of programs running. This setting should only be selected in the event that a malware outbreak is suspected. |
*Please be aware that when Active Protection is disabled, Fail check if scan has not run for: X day(s) is applied. This settings fails the Managed Antivirus Check where a Quick Scan or Deep Scan of the device has not taken place within the specified number of days, up to 30.
Remediation
The Remediation tab specifies what action the Managed Antivirus agent should take when it discovers traces of a threat during a Quick Scan, Deep Scan or Active Protection event.
All threats are categorized and different remediation actions (Allow, Report, Quarantine or Delete) can be set for each category and sub-category.
|
Remediation Level |
Action |
|
Allow |
the threat is allowed to run on the machine and is not reported on |
|
Report |
the threat is allowed to run on the machine and is reported on. |
|
Quarantine |
the threat is placed in quarantine. |
|
Delete |
the threat is completely removed and is unrecoverable. |
Please note that the Report and Delete actions apply to scheduled scans only.
Should Active Protection detect a threat in a category with these actions, it will respectively Allow or Quarantine the threat instead.
For a list of all available threat types please refer to Remediation Options
Allowed Threats
The Allowed Threats tab specifies any programs that although listed in threat definitions are not harmful and should be ignored by Managed Antivirus agent (for example: remote control tools).
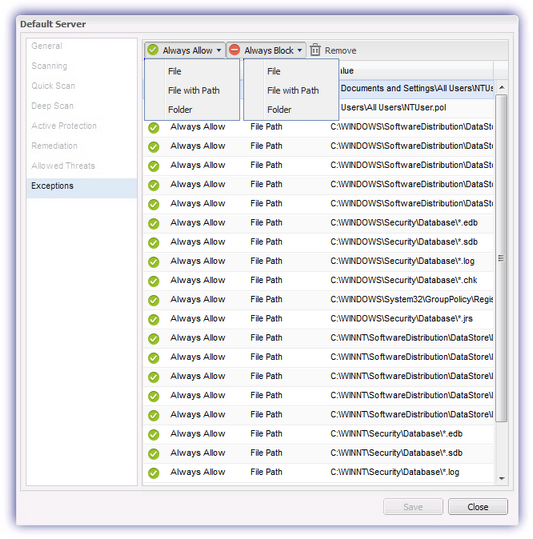
Exceptions
The Exceptions tab specifies files and folders that are to be excluded from scanning (Always Allow) in addition to any files or folders that are considered harmful and will be blocked by the Managed Antivirus agent (Always Block).
Always Allow and Always Block may be configured at the File, File with Path and Folder level, in the returned dialog simply enter the name of the target file, path or folder. Click Save once complete to apply.
|
File |
Enter the name of the file to Always Allow or Always Block. The relevant action will be performed regardless of where the file is located. |
|
File with Path |
Enter a file and its path to Always Allow or Always Block. Please note, the selected action will only be performed where the file is located in this specific path. Where the file is moved to a new location or another file with the same name exists elsewhere the Always Allow or Always Block setting will not be applied to that file. |
|
Folder |
Enter a folder to Always Allow or Always Block Please note, the selected action will only be performed on the folder and its contents where the folder is located in this specific path. Where the folder is moved to a new location or another folder with the same name exists elsewhere the Always Allow or Always Block setting will not be applied to that folder or its contents. |
Please Note: wildcards are supported for exclusions only (Always Allow) and do not include environment variables.
Always Allow Wildcards
|
? |
Matches exactly one character, except the directory separator |
|
* |
Matches zero or more characters, except the directory separator |
Examples of supported entity types:
|
Entity |
Example |
Note |
Always Allow |
Always Block |
|
File Name |
kernel32.dll |
Name of the file, wildcards not permitted. |
||
|
File Name (Pattern) |
*32.dll |
Name of the file, wildcards permitted |
||
|
File with Path |
C:\WINDOWS\system32\kernel32.dll |
Fully specified path to a file, wildcard not permitted |
||
|
File with Path (Pattern) |
C:\WINDOWS\system32\*32.dll |
Fully specified path to a file, wildcard permitted |
||
|
Folder |
C:\WINDOWS\system32\ |
Fully specified path to a file, wildcard not permitted. |
||
|
Folder (Pattern) |
C:\WINDOWS\system*\ |
Fully specified path to a file, wildcard permitted |
||
|
Multiple Path Levels |
*.dll |
Matches: kernel32.dll, advapi32.dll |
||
|
C:\WINDOWS\system32\*.dll |
Matches: C:\WINDOWS\system32\kernel32.dll, C:\WINDOWS\system32\advapi32.dll, etc |
|||
|
?:\WIN*\system*\*.dl |
Matches: C:\WINDOWS\system32\kernel32.dll, D:\WINNT\system\advapi32.dll, etc |
Notes, when entering the location of a Folder this must terminate with a directory separator.
All folder entities are recursive and thus will match the folder itself and any descendant files and folders. For example, C:\WINDOWS\ matches C:\WINDOWS\, C:\WINDOWS\SYSTEM32\, C:\WINDOWS\notepad.exe, C:\WINDOWS\SYSTEM32\regedit.exe, etc
Warning: care must be taken when configuring the Always Block policy settings to ensure important system files or folders are not quarantined (depending on the remediation action specified for Misc category, Misc General sub-category).
Please be aware that Dashboard 6.3 includes the option to migrate a VIPRE Protection Policy for use by the Bitdefender engine with this covered in Protection Policy Migration - VIPRE to Bitdefender Engine with Protection Policy Migration Behavior covering those VIPRE settings that are transferred over.
What do you want to do?
- Review the Managed Antivirus Quick Start Guide
- View Managed Antivirus URLs
- Enable Managed Antivirus on individual servers and workstations or on all servers and workstations at a client or site