Failed Login Check (Hacker Check)
The Failed Login Check queries the Windows Security Event Log to identify the total number of unsuccessful login attempts on the monitored device over the past 24 hours. Where the number of discovered Events exceeds the specified threshold figure the Check fails.
The behavior of the Failed Login Check (including the queried Events, information returned and display format) varies depending on the monitored device's Operating System: pre or post-Windows Vista.
The results of the Failed Login Check are available under the Checks tab of the Dashboard. The Extra column displays the total number of Failed Logins recorded over the last 24 hours, whilst clicking on the Extra link for post-Windows Vista devices opens the More Information dialog containing detailed information on the cause of the failures.
When setting the threshold for the Failed Login Check, we advise you to decide how many failed attempts constitutes an abnormal amount. We recommend liaising with your customer to determine a suitable or expected number of failed logins as a baseline, and then configure the threshold such that if the baseline is exceeded, that the check will fail and send an alert. As each customer is different, and their devices will invariably see different levels of usage and users on a daily basis, we cannot recommend a baseline threshold that will apply to all environments.
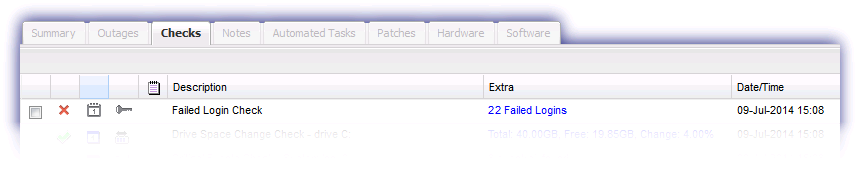
The Failed Login Check was previously known as the Hacker Check with this renamed in Dashboard v5.44.5 to more accurately reflect the Check's function.
Along with the name change an updated version of the Failed Login Check for Windows Vista and later was introduced in Agent 9.7.2 RC. Information on the changes made to the Hacker Check when updating to 9.7.2 RC or later are covered in the below Hacker Check to Failed Login Check section below.
Check configuration
Add
- Select the device in the north pane of the Dashboard
- Go to the Checks tab
- Click Add Check
- Choose Add DSC > Failed Login Check
- Enter the Threshold
- To run an Automated Task when the Check fails choose Assign a Task after creating the Check
- OK to save and apply
- Where Assign a Task after creating the Check is selected:
- Select the script
- Click Next to configure
- Enter the Command Line parameters (if required)
- Set a Script timeout in the range 1 - 3600 seconds (default 120 seconds)
- Click Finish to save and apply
Edit
- Select the device in the north pane of the Dashboard
- Go to the Checks tab
- Select the target Failed Login Check
- From the Check drop-down
- Click Edit Check (also available from the Check's right-click menu)
- Configure the settings
- Click OK to save and apply
Delete
- Select the device in the north pane of the Dashboard
- Go to the Checks tab
- Select the target Failed Login Check
- From the Check drop-down
- Click Delete Check (also available from the Check's right-click menu)
- Enter the password you have logged into the Dashboard under to confirm removal
- Click OK to delete
Failed Login Check- Windows Vista and later
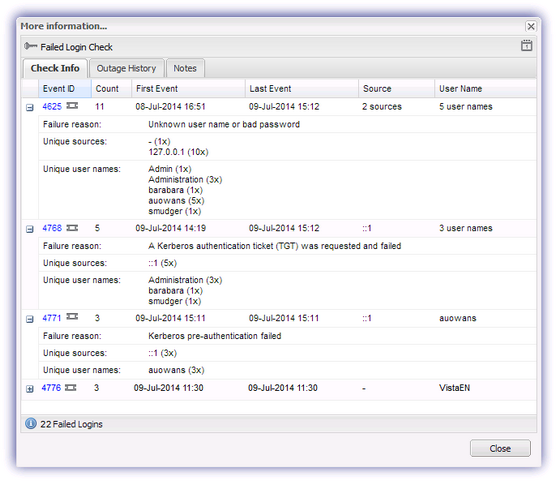
On Windows Vista and later Operating Systems the Failed Login Check returns aggregate data on the IP address and user name associated with the attempted login. Please be aware that the aggregated data is only available for the latest one hundred entries recorded over the monitored period with any number above this simply counted.
The Check achieves this by querying the Windows Security Event Log for any occurrences of the following Events:
|
Event ID |
Failure Type |
|
4625 |
An account failed to log on |
|
4768 |
A Kerberos authentication ticket was requested (when type failure) |
|
4772 |
A Kerberos authentication ticket request failed |
|
4771 |
Kerberos pre-authentication failed |
|
4776 |
The domain controller attempted to validate the credentials for an account |
|
4777 |
The domain controller failed to validate the credentials for an account |
More Information Dialog
The Check Info section of the More Information dialog lists a summary for each discovered Event. Clicking the Event's plus button (+) shows additional detail on the failure, with this detailed view closed with the minus button (-).
|
Information |
Notes |
|
Summary |
|
|
Event ID |
The failure Event ID including a link to EventID.net for further information on this Event type |
|
Count |
Total number of instances of the Event |
|
First Event |
Date and time of first Event |
|
Last Event |
Date and time of last Event |
|
Source |
IP address the attempted login originated from (where known). If there are multiple IP addresses the number of Sources is returned. |
|
User Name |
User name associated with the attempted login. If there are multiple users the number of User names is returned. |
|
Failed Logins |
Total number of Events recorded |
|
Detail |
|
|
Failure reason |
Cause of the failed login attempt |
|
Unique sources |
IP address the attempted login originated from (where known). Includes the number of occurrences of this Event the IP address is associated with. |
|
Unique user names |
User name linked to the attempted login. Includes the number of occurrences of this Event the user name is associated with. |
Failed Login Check - Pre-Windows Vista
The Failed Login Check on pre-Windows Vista Operating Systems returns the total number of occurrences of Events associated with the attempted login.
The Check achieves this by querying the Windows Security Event Log for any occurrences of the following Events:
|
Event ID |
Failure Type |
|
529 |
Unknown user name or bad password |
|
530 |
Account logon time restriction violation |
|
531 |
Account currently disabled |
|
532 |
The specified user account has expired |
|
533 |
User not allowed to logon at this computer |
|
534 |
The user has not been granted the requested logon |
|
535 |
The specified account's password has expired |
|
539 |
Account locked out |
|
548 |
Domain sid inconsistent |
|
644 |
User Account Locked Out |
|
672 |
Authentication Ticket Granted |
|
675 |
Pre-authentication failed |
|
676 |
Authentication Ticket Request Failed (Vista and 2008+) |
|
4625 |
An account failed to log on |
|
4768 |
A Kerberos authentication ticket was requested |
|
4772 |
A Kerberos authentication ticket request failed |
|
4771 |
Kerberos pre-authentication failed |
|
4776 |
The domain controller attempted to validate the credentials for an account |
|
4777 |
The domain controller failed to validate the credentials for an account |
|
Notes |
|
Event IDs 672 and 4768 are only included in the calculation when the Event Type is Failure Audit |
|
Event ID 4625 is supported from Agent 8.4 onwards |
|
Event IDs 4768, 4772, 4771, 4776 and 4777 are supported from Agent 9.7.2 RC onwards |
More Information Dialog
The More Information dialog displays the total number of Failed Logins recorded over the monitored period
Hacker Check to Failed Login Check
The Failed Login Check replaces the Hacker Check from Agent 9.7.2 RC.
To make this transition as seamless as possible the following action is taken when the Daily Safety Check runs for the first time after updating an Agent to 9.7.2 RC (or later).
|
Operating System |
Action taken after the Daily |
|
Windows Vista and later |
Hacker Check automatically upgraded to Failed Login Check |
|
Pre -Windows Vista |
Hacker Check automatically renamed to Failed Login Check |
* Please note, there can be a discrepancy between the naming of the Check on the Dashboard (Failed Login Check) and in the Advanced Monitoring Agent, which may continue to display Hacker Check.
