Port Usage
The architecture diagrams in the following sections show the port usage within an enterprise, with port number references in the relevant tables.
Firewall Considerations in VMware vSphere Environments
Firewall Considerations in Microsoft Hyper-V Environments
Firewall Considerations in Microsoft Azure Environments
Firewall Considerations in AWS Environments
Firewall Considerations in VMware vSphere Environments
Firewall Considerations in VMware vSphere Environments
The following architecture diagram shows the ports that must be opened in the firewalls on all sites.
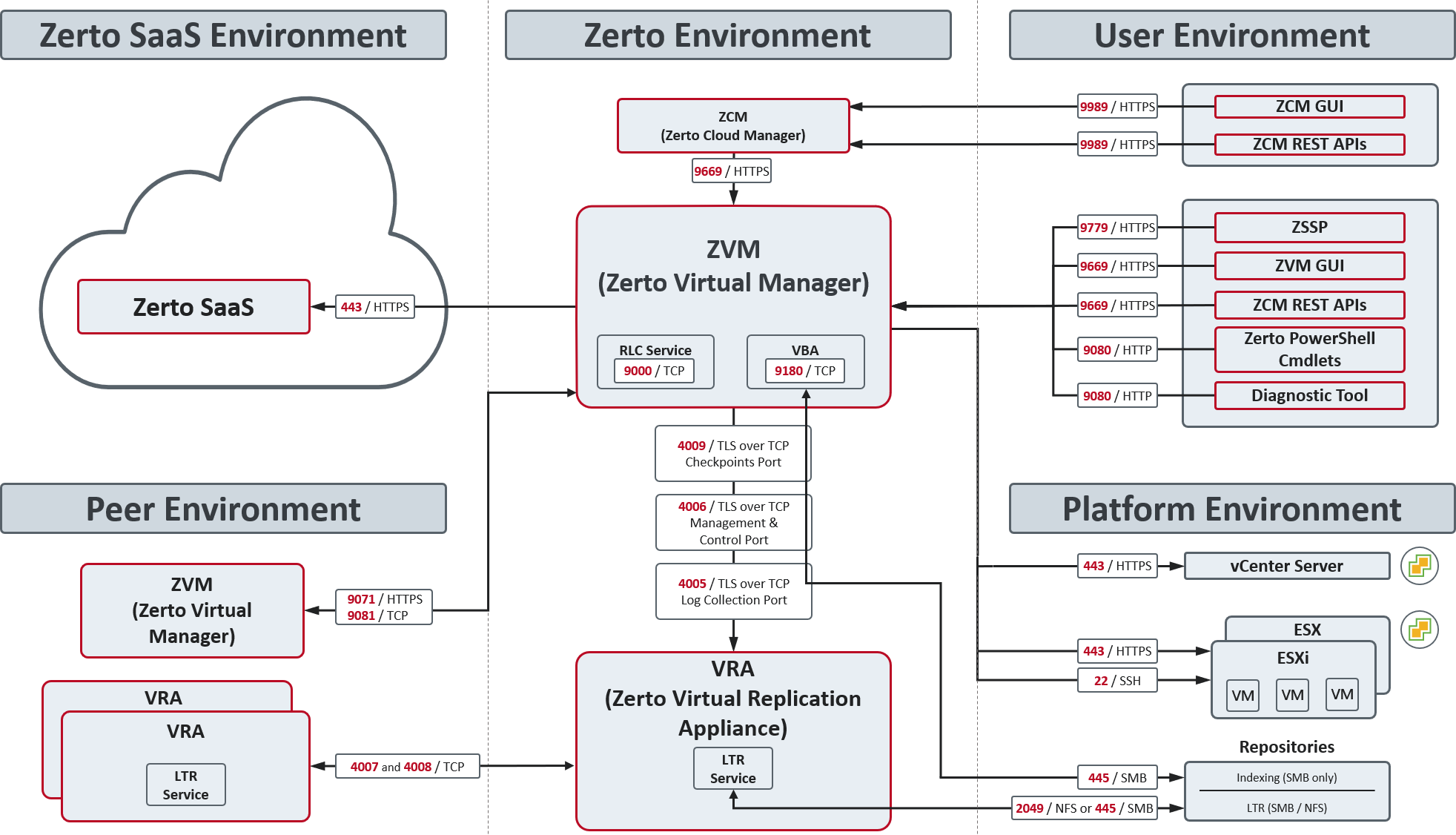
Zerto can be installed at multiple sites and each of these sites can be paired to any of the other sites.
Zerto supports both the protected and recovery sites being managed by a single vCenter Server or System Center Virtual Machine Manager. For example, in the following scenario:
| • | From a branch office, to the main office, both managed by the same System Center Virtual Machine Manager. |
| • | From one host to a second host, both managed by the same System Center Virtual Machine Manager. |
| • | To the same host but using different storage for recovery. |
It is recommended to install Zerto in the main office site where protected machines will be recovered.
The following table provides basic information about the ports shown in the above diagram by Zerto.
Consider firewall rules if the services are not installed on the same network.
| Note: | UDP ports in the 444xx range for DHCP are not required and can therefore be blocked. |
| Port | Purpose | |||
| 22 | Required between an ESXi host and the ZVM during installation of a VRA. | |||
| 443 | Required between the ZVM and the vCenter Server. | |||
| 443 | Required between an ESXi host and the ZVM during installation of a VRA. | |||
| 445 | Required between LTR service and a network shared repository on top of SMB protocol. | |||
| 2049 | Required between LTR service and a network shared repository on top of NFS protocol. | |||
| 4005 | Log collection between the ZVM and site VRAs |
|||
| 4006 |
|
|||
| 4007 | Control communication between protecting and peer VRAs. | |||
| 4008 | Communication between VRAs to pass data from protected virtual machines to a VRA on a recovery site. | |||
| 4009 |
|
|||
| 5672 | TCP communication between the ZVM and vCloud Director for access to AMQP messaging. | |||
| 7073 |
Internal port, used only on the ZVM VM. Used for communication with the service in charge of collecting data for the Zerto Resource Planner.
|
|||
|
9071* |
HTTPS communication between paired ZVMs, when both Zerto versions are 8.0 and above. |
|||
| 9080* |
Communication between the ZVM, Zerto Powershell Cmdlets, and Zerto Diagnostic tool. |
|||
| 9081* | Communication between paired ZVMs** |
|||
| 9180* | Communication between the ZVM and the VBA. | |||
| 9669* | Communication between ZVM and ZVM GUI and ZVM REST APIs, and the ZCM. | |||
| 9989 | Communication between ZCM, and ZCM GUI and ZCM REST APIs. | |||
Firewall Considerations in Microsoft Hyper-V Environments
The following architecture diagram shows the ports that must be opened in the firewalls on all sites.
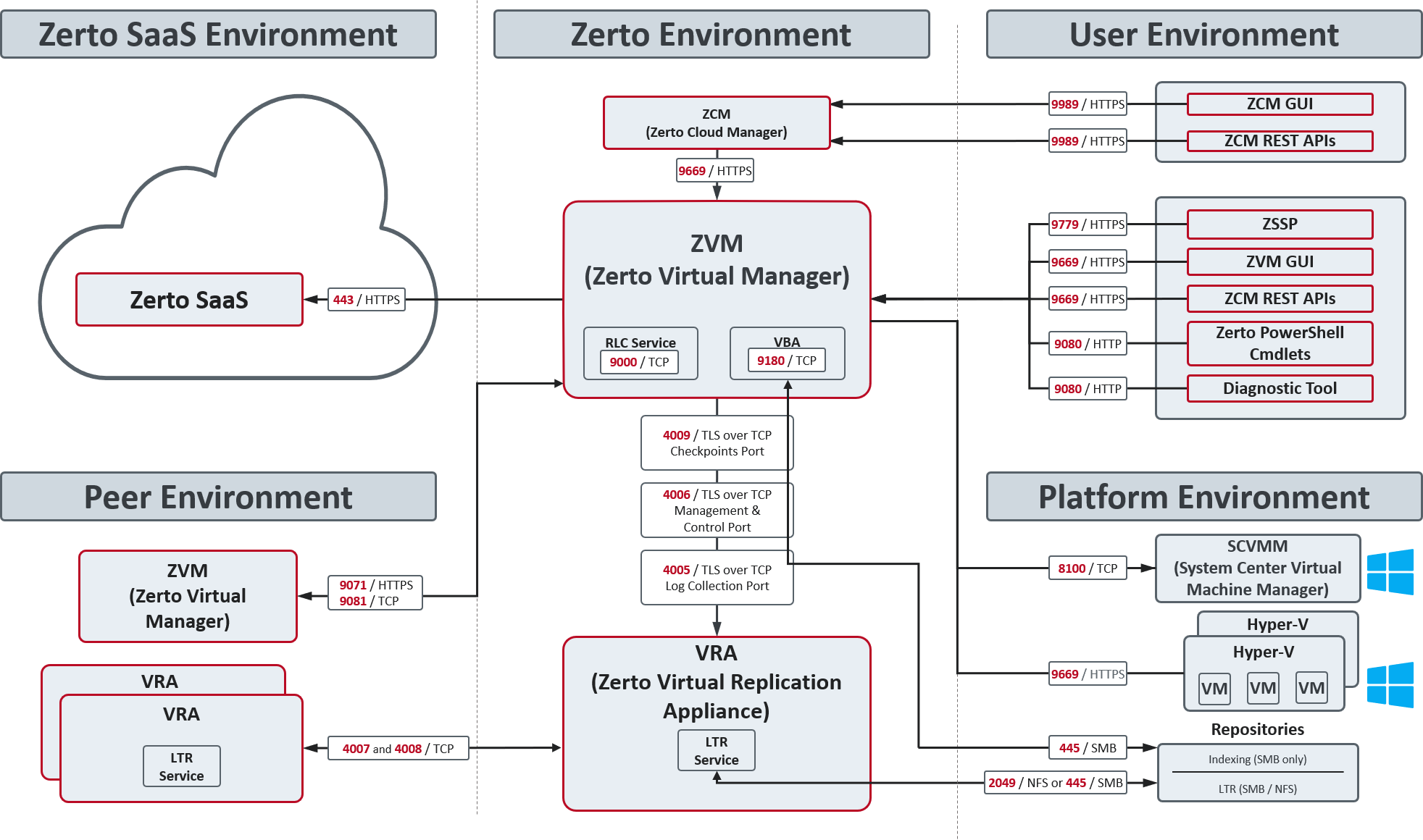
Zerto can be installed at multiple sites and each of these sites can be paired to any of the other sites.
Zerto supports both the protected and recovery sites being managed by a single vCenter Server or System Center Virtual Machine Manager. For example, in the following scenario:
| • | From a branch office, to the main office, both managed by the same System Center Virtual Machine Manager. |
| • | From one host to a second host, both managed by the same System Center Virtual Machine Manager. |
| • | To the same host but using different storage for recovery. |
It is recommended to install Zerto in the main office site where protected machines will be recovered.
The following table provides basic information about the ports shown in the above diagram by Zerto.
Consider firewall rules if the services are not installed on the same network.
The following table provides basic information about the ports shown in the above diagram by Zerto.
| Note: | UDP ports in the 444xx range for DHCP are not required, and can therefore be blocked. |
| Port | Purpose | |||||||||
| 445 | Required between LTR service and a network shared repository on top of SMB protocol. | |||||||||
| 2049 | Required between LTR service and a network shared repository on top of NFS protocol. | |||||||||
| 4005 | Log collection between the ZVM and site VRAs |
|||||||||
| 4006 |
|
|||||||||
| 4007 | Control communication between protecting and peer VRAs. | |||||||||
| 4008 | Communication between VRAs to pass data from protected virtual machines to a VRA on a recovery site. | |||||||||
| 4009 |
|
|||||||||
| 7073 |
Internal port, used only on the ZVM VM. Used for communication with the service in charge of collecting data for the Zerto Resource Planner.
|
|||||||||
| 8100 | Communication between the ZVM and the SCVMM (System Center Virtual Machine Manager). | |||||||||
|
9071* |
HTTPS communication between paired ZVMs, when both Zerto versions are 8.0 and above. |
|||||||||
| 9080* |
Communication between the ZVM, Zerto Powershell Cmdlets, and Zerto Diagnostic tool. |
|||||||||
| 9081* |
Communication between paired ZVMs**
|
|||||||||
|
9180* |
Communication between the ZVM and the VBA. |
|||||||||
|
9669* |
Communication between ZVM and ZVM GUI and ZVM REST APIs, and the ZCM. Communication between every Hyper-V host and the Zerto Virtual Manager. |
|||||||||
| 9779 | Communication between ZVM and ZSSP (Zerto Self Service Portal). | |||||||||
| 9989 | Communication between ZCM, and ZCM GUI and ZCM REST APIs. | |||||||||
Firewall Considerations in Microsoft Azure Environments
The following architecture diagram shows the ports that must be opened in the firewalls on all sites.
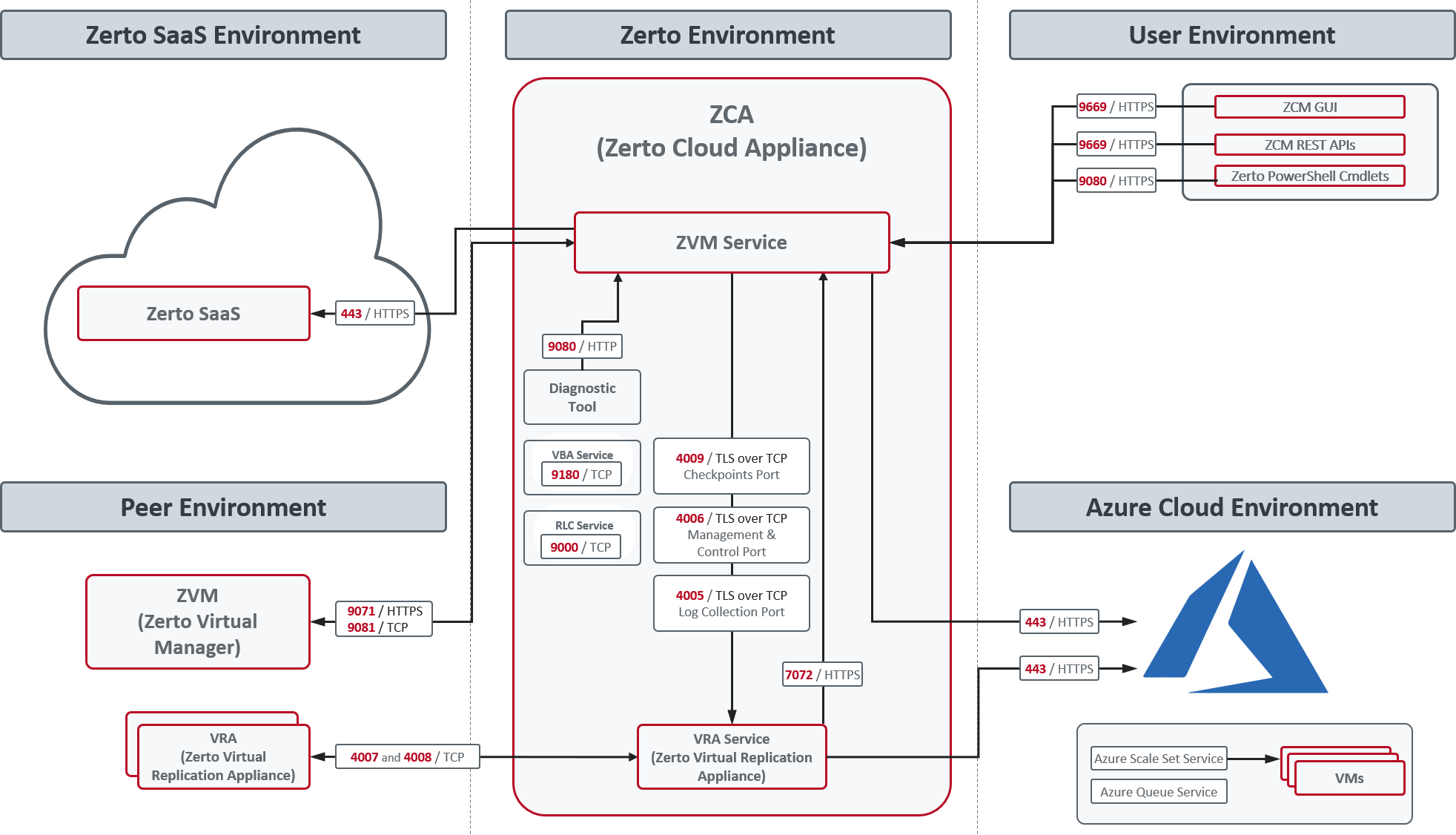
The following table provides basic information about the ports shown in the above diagram by Zerto.
Zerto Cloud Appliance (ZCA) requires the following ports to be open in the Azure site firewall, set in the Azure network security group:
| Port | Description | |||||||||
| 443 |
|
|||||||||
| 4005 | Log collection between the ZVM and site VRAs |
|||||||||
| 4006 |
|
|||||||||
| 4007 | Control communication between protecting and peer VRAs. | |||||||||
| 4008 | Communication between VRAs to pass data from protected virtual machines to a VRA on a recovery site. | |||||||||
| 4009 |
|
|||||||||
| 7072 | Communication between the VRA and ZVM. Required for metadata promotion. | |||||||||
| 7073 |
Internal port, used only on the ZVM VM. Used for communication with the service in charge of collecting data for the Zerto Resource Planner.
|
|||||||||
|
9071* |
HTTPS communication between paired ZVMs, when both Zerto versions are 8.0 and above. |
|||||||||
| 9080* |
Communication between the ZVM, Zerto Powershell Cmdlets, and Zerto Diagnostic tool. |
|||||||||
| 9081* | Communication between paired ZVMs, |
|||||||||
| 9180* | Communication between the ZVM and the VBA. | |||||||||
| 9669* | Communication between ZVM and ZVM GUI and ZVM REST APIs, and the ZCM. | |||||||||
| 9779 | Communication between ZVM and ZSSP (Zerto Self Service Portal). | |||||||||
| 9989 | Communication between ZCM, and ZCM GUI and ZCM REST APIs. | |||||||||
Firewall Considerations in AWS Environments
The following diagram shows Zerto components deployed on one site and the ports and communication protocols used between the components.
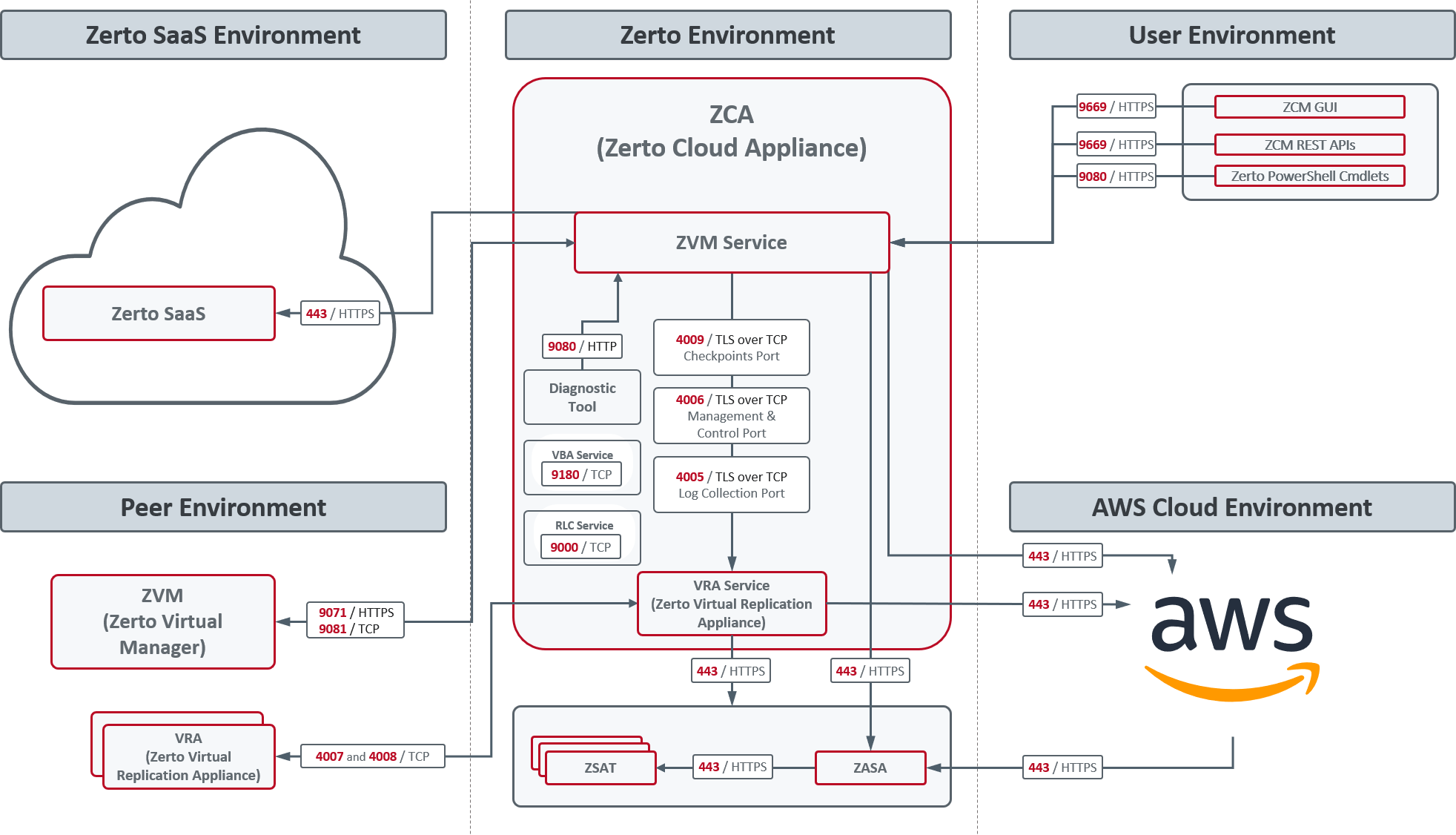
Zerto Cloud Appliance requires the following ports to be open in the AWS site firewall, set in the Amazon security group:
| Port | Description | |||
| 443 | Required between the ZVM and the AWS Cloud environment. | |||
| 443 | Required between ZVM Service and ZASA. | |||
| 4005 | Log collection between the ZVM and site VRAs |
|||
| 4006 |
|
|||
| 4007 | Control communication between protecting and peer VRAs. | |||
| 4008 | Communication between VRAs to pass data from protected virtual machines to a VRA on a recovery site. | |||
| 4009 |
|
|||
| 7073 |
Internal port, used only on the ZVM VM. Used for communication with the service in charge of collecting data for the Zerto Resource Planner.
|
|||
|
9071* |
HTTPS communication between paired ZVMs, when both Zerto versions are 8.0 and above. |
|||
| 9080* |
Communication between the ZVM, Zerto Powershell Cmdlets, and Zerto Diagnostic tool. |
|||
| 9081* | Communication between paired ZVMs** |
|||
| 9180* | Communication between the ZVM and the VBA. | |||
| 9669* | Communication between ZVM and ZVM GUI and ZVM REST APIs, and the ZCM. | |||
| 9779 | Communication between ZVM and ZSSP (Zerto Self Service Portal). | |||
| 9989 | Communication between ZCM, and ZCM GUI and ZCM REST APIs. | |||
Environments with Zerto Cloud Manager
When Zerto is installed on multiple sites, a Zerto Cloud Manager can be used to manage all the sites from one pane of glass for management, orchestration, reporting, and monitoring of recovery operations.
M SP Environments
The following ports must be opened in the firewalls in both the organization and
| Port | # | Description | |||||||||
| 22 | 9, 24 | During Virtual Replication Appliance (VRA) installation on ESXi 5.1 and higher for communication between the Zerto Virtual Manager (ZVM) and the ESXi hosts IPs and for ongoing communication between the ZVM in the cloud site – but not the customer site – and a Zerto Cloud Connector. | |||||||||
| 443 | 2, 6, 8, 19 | During VRA installation on ESX/ESXi hosts for communication between the ZVM and the ESX/ESXi hosts IPs and for ongoing communication between the ZVM and vCenter Server and vCloud Director. | |||||||||
| 4005 | 10 | Log collection between the Zerto Virtual Manager and Virtual Replication Appliances on the same site |
|||||||||
| 4006 | 11 | ||||||||||
| 4007 | 16, 21 | TCP control communication between protecting and recovering VRAs and between a Zerto Cloud Connector and VRAs. | |||||||||
| 4008 | 17, 25 | TCP communication between VRAs to pass data from protected virtual machines to a VRA on a recovery site and between a Zerto Cloud Connector and VRAs. | |||||||||
| 4009 | 12 |
|
|||||||||
| 5672 | 20 | TCP communication between the ZVM and vCloud Director for access to AMQP messaging. | |||||||||
| 7073 |
Internal port, used only on the ZVM VM. Used for communication with the service in charge of collecting data for the Zerto Resource Planner.
|
||||||||||
| 8100 | - | Communication between the Zerto Virtual Manager and the System Center Virtual Machine Manager in a customer site running Zerto Virtual Replication with Hyper-V. | |||||||||
| 9071* | HTTPS communication between paired ZVMs, when both Zerto versions are 8.0 and above. | ||||||||||
| 9080 | 1, 13, 15, 18 |
|
|||||||||
| 9081 | 7, 23, 27 |
TCP communication between Zerto Virtual Managers and between a customer Zerto Virtual Manager and a Zerto Cloud Connector This port must not be changed when providing DRaaS. |
|||||||||
| 9082 and up | 22, 26, 28, 29 |
Two ports for each VRA (one for port 4007 and one for port 4008) accessed via the Zerto Cloud Connector installed by the |
|||||||||
| 9180 | 32 | Communication between the VBA and VRA. | |||||||||
| 9669 | 3, 4, 5, 14 |
HTTPS communication between:
|
|||||||||
| 9779 | 30 | HTTPS communication between the Zerto Self-Service Portal for in-cloud (ICDR) customers and a ZVM. | |||||||||
| 9989 | 31 | HTTPS communication between the browser and the Zerto Cloud Manager. |
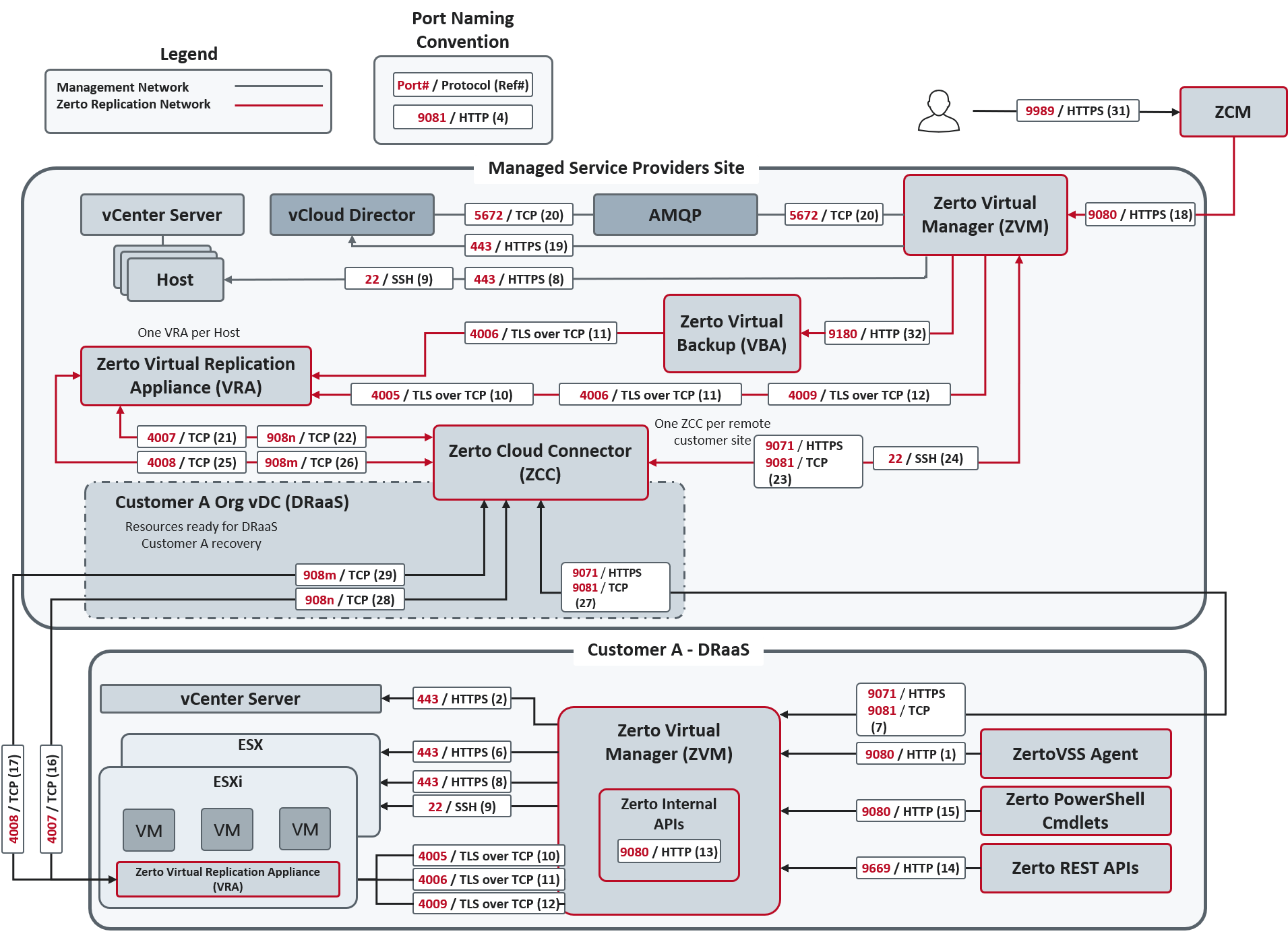
The following architecture diagram shows the port usage when a
